

EnigmaMuseum.com - - HOME:
CRYPTOSYMPOSIUM II
March 20-22, 2014: Charlotte, NC.
This conference was designed to bring together historians and collectors who are interested in cryptology, cryptological history and cryptological machines. It was held in conjunction with the annual Antique wireless Association conference at the Sheraton Airport Hotel in Charlotte, NC. The Conference was organized by
Jim Oram: http://Enigma-Replica.com
This website shows and describes the program, the speakers and their lectures. It also provides links to their powerpoint presentations and to photographs of the extraordinarily wide variety of cryptological devices and documents that were brought to display at the conference.
------------------------------------------
SCROLL Down Page or SELECT from this WEBSITE INDEX:
* * *
OVERVIEW***
* * *
PROGRAM and SPEAKERS***
* * *
LINKS TO PHOTOGRAPHS***
* * *
ADDITIONAL INFORMATION***
OVERVIEW PHOTOGRAPHS


PROGRAM

THURSDAY March 20, 2014
0900 Jim Oram and Ron Lawrence: Introduction:
Jim and Ron welcomed conference attendees.
Jim explained a few changes in the program.
He said that he planned to make video recordings of all sessions.
Ron Lawrence:

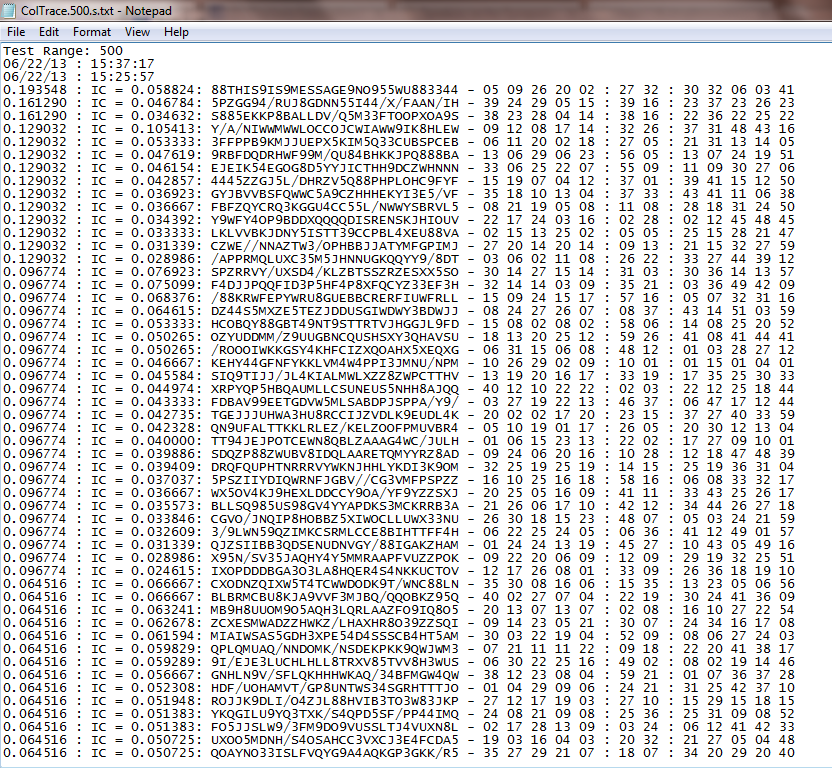
 0915 Jerry McCarthy (UK): Computerized Simulation Techniques of Collossus
0915 Jerry McCarthy (UK): Computerized Simulation Techniques of Collossus
Jerry explained the underlying principles of Collossus and how it was used to decipher messages.
Jerry revisited part of his 2012 presentation in which the math of the Lorenz SZ42/Tunny is explained.
He then showed how his SZ42 simulator can be extended, to demonstrate the operation of Colossus, the machine which was used during WW2 to find the keys of SZ42 messages. The pictures show a screen shot of the resulting Colossus Simulator, and its trace output.
Bio: Jerry McCarthy (UK):
Jerry's day job is to write software, in areas such as cryptography and internationalization, for a global computing company. Jerry says that he is not rich enough to be a full-time cryptocollector, but he is interested in crypto simulation techniques that allow virtual acquisition of crypto hardware without needing to find the space to store it. Jerry's house is definitely not big enough for a Colossus!
Link to Jerry McCarthy's PowerPoint presentation:
http://EnigmaMuseum.com/cryptosymposium14/jerrymccarthy14cs.ppt (2.8MB)
'

 1000 John Alexander (UK): John's Crypto Topics
1000 John Alexander (UK): John's Crypto Topics
John showed and described examples of cryptological machines and explained the difficulties in finding and purchasing them. He showed and described a very unusual Navy M4 Enigma, an unusual Lorenz cipher device, several other devices and a very unusual cryptological device that was brought up from a lake in Germany. He described attempts to discover what the machine does and how it works.
Bio: John Alexander (UK):
For 16 years I was a local police officer with Leicestershire Constabulary. After that I went back to University and trained as a school teacher.
About 18 years ago I began collecting Cipher Systems. These are fascinating in their engineering and use. To open up some rare old machine and get a blast of oil, grease and metal is wonderful. However, at no time in my working life have I ever had access to / use of such systems.
From 2003 to 2011 I had an exhibition at Bletchley Park as 'Enigma and Friends' where I set out to put Enigma into context alongside other systems from the 20th Century.
As a rule of thumb, I consider Enigma models (there are so many) as being in use circa 1920 to 1980 - so there are plenty of contemporary systems to find. Some I will never be permitted access to and this is quite correct. I do what I can.






 1100 Richard Brisson: Cryptocollecting: Opportunities, Challenges, and Issues
1100 Richard Brisson: Cryptocollecting: Opportunities, Challenges, and Issues
Richard described various defining factors behind what we term "crypto-collecting". Why would anyone be motivated to be a crypto-collector? In particular, he pesented a checklist of refined attributes that profile a crypto-collector.
Richard provided further insights in regards to challenges and opportunities which potentially face crypto-collectors such as the Global Network that includes eBay, collector websites, forums, etc. ...And finally, he covered general issues such as collecting with an eye for "return on investment" where return may not necessarily be financial.
Bio: Richard Brisson (Canada):
Richard Brisson is a graduate from the University of Ottawa (B.Sc. Math-Physics in 1978 and M.Sc Systems Science in 1980.
Upon graduation, he was hired by the Communications Security Establishment Canada (CSEC) from which he recently retired. His career at CSEC largely involved duties that encompassed various fields of Mathematics and Computer Science - he is also a graduate of NSA's 3-year Cryptologic Mathematics Program. Over the last 20 years, he has been collecting vintage cryptographic and clandestine artifacts dating up to and including the Cold War.
He has had a number of partnerships in the display of artifacts including the Diefenbunker (Cold War Bunker in Ottawa), National Museum of Science and Technology (in Ottawa), and the National Cryptologic Museum at Fort Meade.
Richard's powerpoint presentations on cryptocollecting may be viewed at:
http://www.campx.ca/powerpoint.html
Some of the pictures that Richard took at the conference may be viewed at:
http://www.campx.ca/Charlotte-2014.html
Richard's website is:
http://www.campx.ca
0200 LUNCH
 1300 Dan and Tom Perera: Real-Time Disassembly and Autopsy of Enigmas
1300 Dan and Tom Perera: Real-Time Disassembly and Autopsy of Enigmas
This session started out with a detailed narrated slide-show that outlined the process of disassembling a working 3-Rotor Enigma to gain access to all of its inner parts. The show emphasized the modular assembly of the Enigma and the ease with which it can be disassembled.
Then, an Enigma that had been immersed in a lake in Northern Germany for 60 years was shown. A narrated autopsy was performed to identify the specific damage and the possible causes of the damage that lead to the death of the machine.
After both shows were completed and any questions answered, Dan demonstrated the disassembly of the Enigma in real-time and pointed to the previously mentioned damaged parts of the recovered Enigma.
Dan Perera's Bio:
Dan earned his MBA from Babson and worked in several businesses before joining EnigmaMuseum.com where he works on Enigma History and Restoration projects.
Link to Tom and Dan Perera's Disassembly PowerPoint presentation:
http://EnigmaMuseum.com/cryptosymposium14/tomperera14diss.ppt (5.3MB)
Link to Dan and Tom's Website: EnigmaMuseum.com
 1400 Debbie Desch Anderson (in absentia): The Dayton Codebreakers
1400 Debbie Desch Anderson (in absentia): The Dayton Codebreakers
Mrs. Anderson was unable to attend so Jim Oram showed the video:
"The Dayton Codebreakers".
It was based on her father's work on the Navy Bombes at the National Cash Register facility in Dayton, Ohio.
For more information please visit website:
http://DaytonCodebreakers.com
...and read the book: "The Secret in Building 26" by Colin Burke and Jim DeBrosse published by Random House in 2004.
 1500 David Kahn: How I Discovered World War II's Greatest Spy
1500 David Kahn: How I Discovered World War II's Greatest Spy
David Kahn described his latest book by explaining how he discovered the identity of the man who sold the key information about Germany’s Enigma machine during World War II that enabled Polish and then British codebreakers to read the secret German Enigma-coded messages.
David Kahn's Bio:
David Kahn is universally regarded as the dean of intelligence historians. He is the author of Seizing the Enigma: The Race to Break the German U-Boats Codes, 1939-1943. His pathbreaking book The Codebreakers, the classic history of codemaking and codebreaking remains in stalwart print 45 years after its publication (portions have been updated). The Codebreakers comprehensively chronicles the history of cryptography from ancient Egypt to the time of its writing. It is widely regarded as the best account of the history of cryptography up to its publication.
He is also the co-founder of the Taylor & Francis journal, Cryptologia, which continues to attract new subscribers. He holds a Ph.D. in Modern History from Oxford and lives in Great Neck, New York. (From an Amazon write-up)
David Kahn's Website contains a wealth of information: http://David-Kahn.com
 1600 Ralph Simpson: One-Time Pad Encryption Techniques
1600 Ralph Simpson: One-Time Pad Encryption Techniques
Ralph Simpson described and explained the One-Time Pad, widely thought to be the only truly unbreakable enciphering technique. He gave examples of its use and showed examples of actual pads.
Ralph Simpson's Bio:
Ralph Simpson worked in the computer industry in a variety of technical and management positions for 32 years, writing a book on high availability systems at IBM and starting up the European support organization for Cisco Systems. He retired in 2009 as Senior Director of Professional Services at Cisco Systems. After living in 10 states and 5 countries, Ralph has settled in Silicon Valley with his wife of 41 years and 3 grown children. He is now a volunteer at a history museum and an avid collector of cipher machines. He has a website called CipherMachines.com and is currently writing a book titled
..."Cipher Machines: the History and Technology of Cryptology".
Link to Ralph Simpson's One-Time-Pad PowerPoint presentation:
http://EnigmaMuseum.com/cryptosymposium14/ralphsimpson14cs.ppt (3,7MB)
Link to Ralph Simpson's general Enigma-related PowerPoint presentation:
http://ciphermachines.com/enigma_files/enigma.ppt
Link to Ralph Simpson's PowerPoint presentation about cipher machines:
http://ciphermachines.com/TypesofCipherMachines.ppt
1730 DINNER, Social Time, Viewing of Cipher Machine Displays.
FRIDAY March 21, 2014
 0900 Glen Miranker: Enigmas in the Battle of the Atlantic: Did it make a Difference?
0900 Glen Miranker: Enigmas in the Battle of the Atlantic: Did it make a Difference?
Glen presented a quick overview of the Battle of the Atlantic and then led us directly into a time-based analysis of allied shipping losses during the war using a graph with the entire war on its horizontal axis. He then superimposed various factors onto the graph so that the audience could see the relationships between these factors and the sinkings. He included such factors as the number of U-Boats operating, the number of U-Boats sunk, the Development of Radio Direction-Finding, and the periods of the war when Enigma-encoded messages were being read. This technique of analysis gave the audience the ability to directly observe the relationships between each of these factors and Allied shipping losses. A link to this presentation is included below his bio:
Bio: Glen Miranker: USA 2014
Glen S. Miranker made a career in computer start-up companies (retiring as chief technology officer for
hardware at Apple Computer in 2005) and now pursues two long-standing passions: a book collection
devoted to Sherlock Holmes and the history of cryptography.
Active in research and preservation projects connected with wartime cryptography in the U.S., he consults
frequently with the National Cryptologic Museum (Ft. Meade, MD).
Education:
BA (Summa Cum Laude, Tau Beta Pi) Computer Science, 1975, Yale College
MS Computer Science, 1977,
Massachusetts Institute of Technology
PhD Computer Science, 1979
Massachusetts Institute of Technology
1976–1979 Academic Positions:
Adjunct Professor in Computer Science, 1979–1981, Columbia University
Adjunct Professor in Computer Science, 1984–1985, University of California, Berkeley.
Corporate Experience:
Research Staff Member 1979–1981 IBM Research, Yorktown, NY
Numerous computer-related startup companies 1981–1996
Vice-President Hardware Systems Development 1996–2003 Apple Computer, Inc.
Chief Technology Officer (Hardware), 2003–2005 Apple Computer, Inc.
He has restored a WWII German naval Enigma machine and assisted in preservation work (including the fabrication of replica Enigma bulbs) at such organizations as Bletchley Park and Communications Security Establishment Canada.
Link to Glen's presentation:
http://EnigmaMuseum.com/cryptosymposium14/glen/
Please use the right-arrow key or space bar to sequence through the features of each slide and transition to the next slide.
 1000 Tom Perera: Enigma Declasssified: New Discoveries, TICOM, NeuroCryptology, Alan Turing, and SABOTAGE
1000 Tom Perera: Enigma Declasssified: New Discoveries, TICOM, NeuroCryptology, Alan Turing, and SABOTAGE
Tom started out by describing the work and techniques used by some of the historians working on uncovering additional details about Enigma History. He traced the known models of the Enigma as shown in the chart constructed by Paul Reuvers, Mark Simons and Frode Weierud. He showed some recently discovered Enigma models and then he showed some recently discovered photos of the Enigma in Action from
Helge Fykse's webpages: http://www.laud.no/ww2.
He then described the evolving TICOM information as historians struggle to work their way through the 20,000 pages of information.
Then Tom used the Psychological technique of Implicit Personality Theory to give people a chance to meet Alan Turing's personality by looking at a wide ranging set of photos of Turing taken at various stages in his life. He emphasized a photo of Turing laughing and juxtaposed it next to a discussion of Turing's contributions to chaos theory and Neurocryptology (Banburisimus in the brain) in which the deciphering processes of the human brain are compared with Turing's strategies in deciphering Enigma messages. He mentioned Jerzy Rozycki's clock method of sequential analysis and the de Brujin sequences and hash codes and suggested that Turing's picture showed him laughing at us as we tried to undestand his complex mathematical theorizing.
Tom then showed some of the many variations and oddities in Enigma design. He concluded by showing several examples of how Enigmas were sabotaged in the factories in which they were made. He showed mechanical sabotage and several examples of electrical sabotage in which the Enigmas would pass initial testing but fail later in the field.
Bio: Tom Perera: Vermont, USA\
Tom Perera received his doctorate from Columbia University, He taught and researched in the field of Brain Science and Coding Strategies of the Nervous System at Columbia and Montclair State Universities for 35 years. He has been hunting for, collecting, studying, writing about, and lecturing on the German Enigma for over 25 years.
Link to Tom Perera's PowerPoint presentation:
http://EnigmaMuseum.com/cryptosymposium14/tomperera14new.ppt (8.0MB)
Tom's website:
http://EnigmaMuseum.com
 1100 Marc Tessier: "Kickstarter Enigma Project"
1100 Marc Tessier: "Kickstarter Enigma Project"
Marc Tessier: The-Open-Enigma-Project;
Marc and his company have developed an Open-Software/Open-Hardware version of the Enigma using the Arduino microprocessor platform.
It can be used to duplicate the functions of all models of the Enigma. Their machine can encrypt and decrypt any information you wish using what is still today a very secure key. Their device can be reprogrammed at will and it can even be used to simply display a scrolling marquee of any text message on its unique LED displays.
The Kickstarter Website:
1200 Lunch
 1300 Craig Bauer Cryptanalysis of Enigma
1300 Craig Bauer Cryptanalysis of Enigma
Craig Bauer traced in detail the techniques of the original work by the Polish Mathematicians in discovering the wiring of the rotors and deciphering Enigma-Enciphered messages.
Craig Bauer: Bio:
Craig Bauer is Associate Professor of Mathematics at York College of Pennsylvania
Please see his website below for further details:
Link to Craig Bauer's PowerPoint presentation:
http://EnigmaMuseum.com/cryptomuseum14/bauer14.ppt
Link to Craig Bauer's website: http://faculty.ycp.edu/~cbauer/
 1400 David Hatch: The NSA Museum
1400 David Hatch: The NSA Museum
David Hatch gave a detailed explanation of the use of native languages to secure communications down through military history. He discussed these techniques as used in the American Civil War, WW-I and WW-II.
He described the roles played by the Choctaw, Navaho, Commanche, Hopi and other native American tribes in various wars and theatres. He explained the term "codetalkers" as being not only the communication in native languages but the use of codes to represent and disguise words.
David Hatch: Bio:
Technical Director of the Center for Cryptologic History: National Security Agency
Technical Director: Center for Cryptologic History
Chief of the Operational History Division: Center for Cryptologic History
Technical Director and Principal Historian: National Security Agency's Center for Cryptologic History
 1500 Nicholas Gessler: Duke University
1500 Nicholas Gessler: Duke University
Nicholsa Gessler brought a very wide variety of early and unusual historic cipher devices and documents.
He described two very early examples of ciphers and his attempts to find more information about them.
The first was a French cipher disc that carried the name: Nicholas Dionne.
It may be the earliest known example of a polyalphabetic cipher disc.
He explained various hypotheses about its use.
The second was the "1777 Aspinwall Cipher: A Tory Diplomatic Code from the Revolutionary War".
He outlined and explained his attempts to research and find its origins.
.
Nicholas Gessler's Bio: https://web.duke.edu/isis/gessler/cv-pubs/cv.htm
Nicholas Gessler's Website: https://web.duke.edu/isis/gessler/
 1600 Elonka Dunin: Kryptos and the Cyrillic Projector Ciphers
1600 Elonka Dunin: Kryptos and the Cyrillic Projector Ciphers
Elonka Dunin is co-founder and co-leader of a group of cryptographers who are working hard to crack a code on the famous Kryptos sculpture at CIA Headquarters.
The ciphers on the Cyrillic Projector here in Charlotte, were cracked in 2003 by an international team spearheaded by Elonka Dunin. Kryptos and the Cyrillic Projector have nearly identical styles of shifted alphabet tables.
Elonka explained how the code was cracked and the current state of knowledge about the Kryptos sculpture, its own encrypted messages, and its mysterious CIA surroundings.
Bio: Elonka Dunin: http://elonka.com
Elonka Dunin's Website: http://elonka.com
 1800 Banquet Dinner Talk:
1800 Banquet Dinner Talk:
Professor I. M. A. Knowitall: The Psychology of Collecting
The World in-famous Dr. Knowitall explained the evolutionary, physiological, and childhood-based factors that drive people to collect. He showed examples of people who had tried to 'kick the habit' and he explained various therapeutic interventions for out-of-control collecting.
Link to Dr. Knowitall's PowerPoint presentation: tomperera14psych.ppt (4,2MB)
SATURDAY March 22, 2014
 0900 Klaus Schmeh: Encrypted Books: Mysteries That Fill Hundreds of Pages.
0900 Klaus Schmeh: Encrypted Books: Mysteries That Fill Hundreds of Pages.
In his talk, Klaus presented the ten most interesting encrypted books that he is aware of. Among others, he addressed the Voynich Manuscript, the Rohonc Codex, the Folger Manuscript, and the Action Line Cryptogram. His ten examples came from a list of over 40 encrypted books that he has published on his web site:
http://scienceblogs.de/klausis-krypto-kolumne/klaus-schmehs-list-of-encrypted-books/
Bio: Klaus Schmeh
Klaus Schmeh (born in 1970) is a German computer scientist and crypto expert. He has written ten books and over 150 articles about cryptology (mostly in German). Klaus is a member of the editorial board of Cryptologia. His German blog "Klausis Krypto Kolumne" is about historical cryptology:
http:www.schmeh.org
 1000 Tom Perera: Adventures in Enigmaville: The Excitement of the Hunt for Enigmas and Information
1000 Tom Perera: Adventures in Enigmaville: The Excitement of the Hunt for Enigmas and Information
Tom focused this talk on the excitement of the hunt for Enigmas and Enigma History. He started out by explaining how his 60-years of telegraph collecting led him to a radio meet in Friedrichshafen Germany where he found his first Enigma and FIALKA. Tom showed
pictures of the Friedrichshafen meets and some of the amazing machines that are brought to the show each year.
He explained that he has been expanding the number of cryptocollectors tables and encouraging crypto collectors and historians to attend and bring their machines. His First Annual Enigma Forum drew a standing-room only crowd and his Second Annual Forum promises to attract an even larger attendance.
He also showed Enigmas at some of the WW-II reenactments and described the discovery of an extremely rare code book cover at a reenactment.
He went on to describe and show examples of hunts for Enigmas in Lakes, U-Boats, Attics, Basements, Historic Sites, and Museums. He described a daring daylight raid on an historic site to recover artifacts before the site was destroyed. He was armed with a variety of tools (see picture) that he used to penetrate the defenses and extract the artifacts. He ended his talk by describing the secret spy room in Bergen, Norway in which the "Theta" organization of spies reported German ship and troop deployments to the Allied forces during the war.
Bio: Tom Perera: Vermont, USA\
Tom Perera received his doctorate from Columbia University, He taught and researched in the field of Brain Science and Coding Strategies of the Nervous System at Columbia and Montclair State Universities for 35 years. He has been hunting for, collecting, studying, writing about, and lecturing on the German Enigma for over 25 years.
Link to Tom Perera's Enigma Adventures PowerPoint presentation:
http://EnigmaMuseum.com/cryptosymposium14/tomperera14adv.ppt (11.0MB)
Tom's website:
http://EnigmaMuseum.com
1100 Social Time. View and Explain Exhibits. Networking.
1200 Lunch
 1400 Elonka Dunin: Geocaching and Criptography
1400 Elonka Dunin: Geocaching and Criptography
Elonka explained the technique of combining Geocaching techniques with cryptanalysis.
Bio: Elonka Dunin: http://elonka.com
Elonka Dunin's Website: http://elonka.com
 1500 Jim Oram: Field Trip To Enigma-Replica.com shop
1500 Jim Oram: Field Trip To Enigma-Replica.com shop
Jim's website:
http://Enigma-Replica.com
1600 Elonka Dunin: Field Trip to UNC
The ciphers on the Cyrillic Projector here in Charlotte, were cracked in 2003 by an international team spearheaded by Elonka Dunin. Elonka hosted a field trip out to UNC to take a look at the sculpture itself
Bio: Elonka Dunin: http://elonka.com
Elonka Dunin's Website: http://elonka.com
Links to photographs of the conference:
Jim Oram's Photographs: ( Jim Oram was the Conference Organizer )
Jim will be posting and updating pictures and videos on the conference website:
http://cryptosymposium.com
Ralph Simpson's Photographs:
http://ciphermachines.com/photos/index.php/2014-Charlotte-Cryptologic-Symposium

Mark Sims' Reproduction Programming cards for FIALKA and Transvertex HC-9
This picture shows reproduction programming cards for the FIALKA (Left) and HC-9 (Right) that were made by Mark Sims and that were on display at the conference.
Mark can make them to order and he can also make a FIALKA card that maps the alphabet to itself if you don't have the metal triangle. He may also be able to supply the metal triangles. You may contact him at email: holrum(at)hotmail.com.
CONTACT INFORMATION - -
Email: Info@EnigmaMuseum.com
Tom Perera Ph. D.
Professor Emeritus: Montclair State University
Curator: EnigmaMuseum.com
COPYRIGHT NOTICE: (Copyright (c) 2014: Tom Perera Ph. D.)
Although all the pictures and text are copyrighted, you may use any of them
for your own personal applications including public lectures and
demonstrations, publications and websites as long as you mention the
www.EnigmaMuseum.com or w1tp.com/enigma Museum. If you plan to offer them for sale to the public
in any form, you must email me for permission which I will generally grant as
long as you mention my museums: http://EnigmaMuseum.com or http://w1tp.com/enigma. My email address is
given above. Some of the material may require contacting
other copyright owners for commercial use and I will inform you by email.
Please also see the disclaimer of warranty.






 0915 Jerry McCarthy (UK): Computerized Simulation Techniques of Collossus
0915 Jerry McCarthy (UK): Computerized Simulation Techniques of Collossus


 1000 John Alexander (UK): John's Crypto Topics
1000 John Alexander (UK): John's Crypto Topics






 1100 Richard Brisson: Cryptocollecting: Opportunities, Challenges, and Issues
1100 Richard Brisson: Cryptocollecting: Opportunities, Challenges, and Issues
 1300 Dan and Tom Perera: Real-Time Disassembly and Autopsy of Enigmas
1300 Dan and Tom Perera: Real-Time Disassembly and Autopsy of Enigmas
 1400 Debbie Desch Anderson (in absentia): The Dayton Codebreakers
1400 Debbie Desch Anderson (in absentia): The Dayton Codebreakers
 1500 David Kahn: How I Discovered World War II's Greatest Spy
1500 David Kahn: How I Discovered World War II's Greatest Spy
 1600 Ralph Simpson: One-Time Pad Encryption Techniques
1600 Ralph Simpson: One-Time Pad Encryption Techniques
 0900 Glen Miranker: Enigmas in the Battle of the Atlantic: Did it make a Difference?
0900 Glen Miranker: Enigmas in the Battle of the Atlantic: Did it make a Difference?
 1000 Tom Perera: Enigma Declasssified: New Discoveries, TICOM, NeuroCryptology, Alan Turing, and SABOTAGE
1000 Tom Perera: Enigma Declasssified: New Discoveries, TICOM, NeuroCryptology, Alan Turing, and SABOTAGE
 1100 Marc Tessier: "Kickstarter Enigma Project"
1100 Marc Tessier: "Kickstarter Enigma Project"
 1300 Craig Bauer Cryptanalysis of Enigma
1300 Craig Bauer Cryptanalysis of Enigma
 1400 David Hatch: The NSA Museum
1400 David Hatch: The NSA Museum
 1500 Nicholas Gessler: Duke University
1500 Nicholas Gessler: Duke University
 1600 Elonka Dunin: Kryptos and the Cyrillic Projector Ciphers
1600 Elonka Dunin: Kryptos and the Cyrillic Projector Ciphers
 1800 Banquet Dinner Talk:
1800 Banquet Dinner Talk: 0900 Klaus Schmeh: Encrypted Books: Mysteries That Fill Hundreds of Pages.
0900 Klaus Schmeh: Encrypted Books: Mysteries That Fill Hundreds of Pages.
 1000 Tom Perera: Adventures in Enigmaville: The Excitement of the Hunt for Enigmas and Information
1000 Tom Perera: Adventures in Enigmaville: The Excitement of the Hunt for Enigmas and Information
 1400 Elonka Dunin: Geocaching and Criptography
1400 Elonka Dunin: Geocaching and Criptography
 1500 Jim Oram: Field Trip To Enigma-Replica.com shop
1500 Jim Oram: Field Trip To Enigma-Replica.com shop